Latest Posts
New phishing techniques target Gmail users. Here's how to spot them before you become a victim.
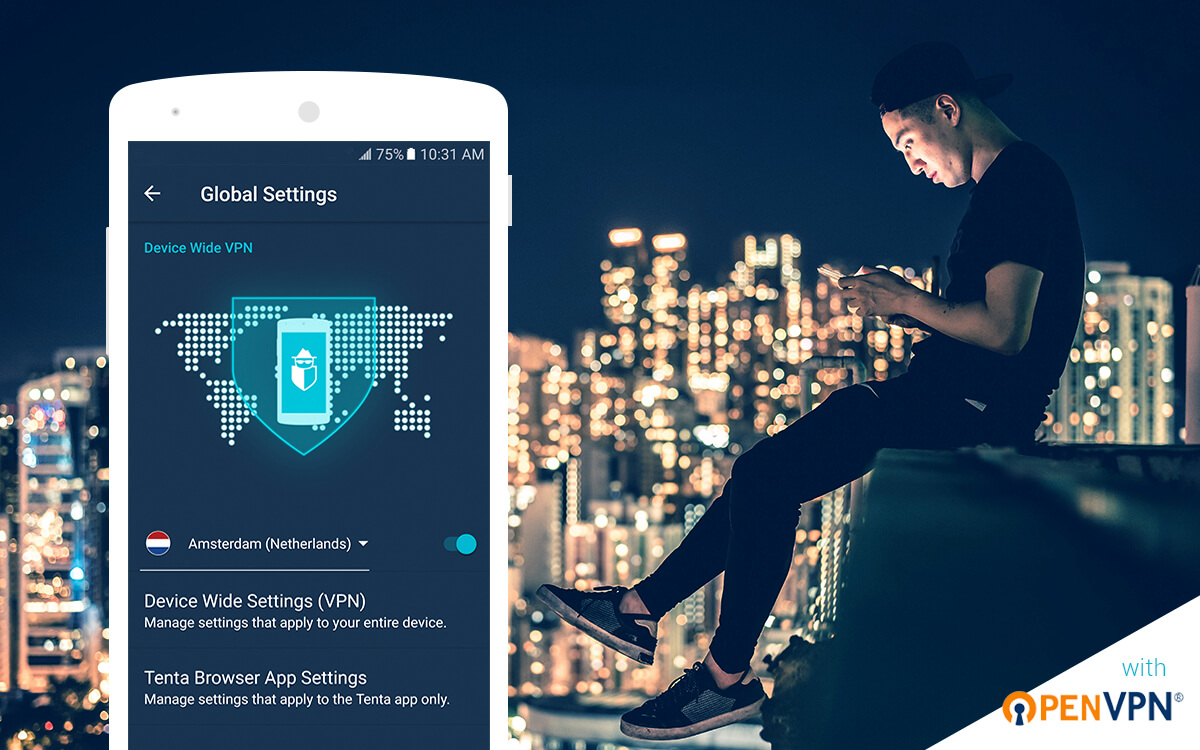
Private browsing mode isn't as private as it should be. We think we can make it better but we need your help. Join Tenta's opt-in beta program on Google Play and help us test our latest privacy features, such as Device Wide VPN and Tenta Secure DNS.
Under current law (which was passed in 1986), the government can access your cloud storage without a warrant. Scary — but a bill named the Email Privacy Act recently reintroduced in the House is trying to change that.
Following a trend of increased internet censorship in the Middle East, the Egyptian government blocked the secure messaging app Signal at the end of last year.
Take a second to think about just how important — and personal — the data on your phone is. Now ask yourself, Am I protecting it properly? If you’re even a little bit unsure, follow these eight tips for protecting your smartphone.
We've expanded Tenta Browser's built in VPN to provide even more protection. Opt-in beta testers can now use Device Wide VPN and Per Zone VPN free for a limited time.
You might know that websites are tracking the sites you're using, but did you know they're also tracking your exact location? That's just the start, though, because the websites you're visiting know much more about you than you think.
The concept of holding someone for ransom is a familiar part of our cultural lexicon at this point. We've all seen the movies - someone gets kidnapped, the kidnappers call with a demand, the hero raises to rescue the victim before it's too late. But these days, a more realistic storyline would be not about holding a person for ransom but instead about holding someone's data for ransom. It's called ransomware, and here's how to protect yourself from it.
The Investigatory Powers Bill, commonly referred to as the Snooper's Charter, became an act on December 3, 2016, despite being heavily petitioned by UK citizens concerned about increased online surveillance.